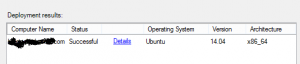
The feature names in DISM are a bit different to those in PowerShell. You can see what they are from a booted computer with the following command:
dism /online /get-features
However I find it useful to keep a searchable list around as it is faster to use to try and remember/work out what that feature is actually called when you are trying to add it to a wim file or computers and the install-windowsfeature is not working for you.
Here is a list of all features from an up to date 2012 R2 Standard computer:
Feature Name : NetFx4ServerFeatures
Feature Name : NetFx4
Feature Name : NetFx4Extended-ASPNET45
Feature Name : MicrosoftWindowsPowerShellRoot
Feature Name : MicrosoftWindowsPowerShell
Feature Name : ServerCore-FullServer
Feature Name : IIS-WebServerRole
Feature Name : IIS-WebServer
Feature Name : IIS-CommonHttpFeatures
Feature Name : IIS-Security
Feature Name : IIS-RequestFiltering
Feature Name : IIS-StaticContent
Feature Name : IIS-DefaultDocument
Feature Name : IIS-DirectoryBrowsing
Feature Name : IIS-HttpErrors
Feature Name : IIS-HttpRedirect
Feature Name : IIS-WebDAV
Feature Name : IIS-ApplicationDevelopment
Feature Name : IIS-WebSockets
Feature Name : IIS-ApplicationInit
Feature Name : IIS-NetFxExtensibility
Feature Name : IIS-NetFxExtensibility45
Feature Name : IIS-ISAPIExtensions
Feature Name : IIS-ISAPIFilter
Feature Name : IIS-ASPNET
Feature Name : IIS-ASPNET45
Feature Name : IIS-ASP
Feature Name : IIS-CGI
Feature Name : IIS-ServerSideIncludes
Feature Name : IIS-HealthAndDiagnostics
Feature Name : IIS-HttpLogging
Feature Name : IIS-LoggingLibraries
Feature Name : IIS-RequestMonitor
Feature Name : IIS-HttpTracing
Feature Name : IIS-CustomLogging
Feature Name : IIS-ODBCLogging
Feature Name : IIS-CertProvider
Feature Name : IIS-BasicAuthentication
Feature Name : IIS-WindowsAuthentication
Feature Name : IIS-DigestAuthentication
Feature Name : IIS-ClientCertificateMappingAuthentication
Feature Name : IIS-IISCertificateMappingAuthentication
Feature Name : IIS-URLAuthorization
Feature Name : IIS-IPSecurity
Feature Name : IIS-Performance
Feature Name : IIS-HttpCompressionStatic
Feature Name : IIS-HttpCompressionDynamic
Feature Name : IIS-WebServerManagementTools
Feature Name : IIS-ManagementConsole
Feature Name : IIS-LegacySnapIn
Feature Name : IIS-ManagementScriptingTools
Feature Name : IIS-ManagementService
Feature Name : IIS-IIS6ManagementCompatibility
Feature Name : IIS-Metabase
Feature Name : IIS-WMICompatibility
Feature Name : IIS-LegacyScripts
Feature Name : IIS-FTPServer
Feature Name : IIS-FTPSvc
Feature Name : IIS-FTPExtensibility
Feature Name : WAS-WindowsActivationService
Feature Name : WAS-ProcessModel
Feature Name : WAS-NetFxEnvironment
Feature Name : WAS-ConfigurationAPI
Feature Name : IIS-HostableWebCore
Feature Name : BITSExtensions-AdminPack
Feature Name : Gateway-UI
Feature Name : MSMQ
Feature Name : MSMQ-Services
Feature Name : MSMQ-Server
Feature Name : MSMQ-Triggers
Feature Name : MSMQ-ADIntegration
Feature Name : MSMQ-HTTP
Feature Name : MSMQ-Multicast
Feature Name : MSMQ-DCOMProxy
Feature Name : MSMQ-RoutingServer
Feature Name : WCF-Services45
Feature Name : WCF-HTTP-Activation45
Feature Name : WCF-TCP-Activation45
Feature Name : WCF-Pipe-Activation45
Feature Name : WCF-MSMQ-Activation45
Feature Name : WCF-TCP-PortSharing45
Feature Name : ManagementOdata
Feature Name : DSC-Service
Feature Name : IdentityServer-SecurityTokenService
Feature Name : Application-Server
Feature Name : AS-NET-Framework
Feature Name : Application-Server-WebServer-Support
Feature Name : AS-Ent-Services
Feature Name : Application-Server-TCP-Port-Sharing
Feature Name : Application-Server-WAS-Support
Feature Name : Application-Server-HTTP-Activation
Feature Name : Application-Server-MSMQ-Activation
Feature Name : Application-Server-TCP-Activation
Feature Name : Application-Server-Pipe-Activation
Feature Name : AS-Dist-Transaction
Feature Name : AS-Incoming-Trans
Feature Name : AS-Outgoing-Trans
Feature Name : AS-WS-Atomic
Feature Name : ADCertificateServicesRole
Feature Name : CertificateServices
Feature Name : OnlineRevocationServices
Feature Name : WebEnrollmentServices
Feature Name : NetworkDeviceEnrollmentServices
Feature Name : CertificateEnrollmentPolicyServer
Feature Name : CertificateEnrollmentServer
Feature Name : Web-Application-Proxy
Feature Name : IPAMServerFeature
Feature Name : RightsManagementServices-Role
Feature Name : RightsManagementServices
Feature Name : RMS-Federation
Feature Name : RightsManagementServices-AdminTools
Feature Name : WSS-Product-Package
Feature Name : BITSExtensions-Upload
Feature Name : Printing-Server-Foundation-Features
Feature Name : Printing-Server-Role
Feature Name : Printing-LPDPrintService
Feature Name : BusScan-ScanServer
Feature Name : Printing-InternetPrinting-Server
Feature Name : HCAP-Server
Feature Name : HCSRuntime
Feature Name : RemoteAccess
Feature Name : RemoteAccessServer
Feature Name : RasRoutingProtocols
Feature Name : WCF-HTTP-Activation
Feature Name : WCF-NonHTTP-Activation
Feature Name : WindowsPowerShellWebAccess
Feature Name : RPC-HTTP_Proxy
Feature Name : Smtpsvc-Admin-Update-Name
Feature Name : Smtpsvc-Service-Update-Name
Feature Name : Gateway
Feature Name : WebAccess
Feature Name : Microsoft-Windows-Web-Services-for-Management-IIS-Extension
Feature Name : WorkFolders-Server
Feature Name : UpdateServices
Feature Name : UpdateServices-Services
Feature Name : UpdateServices-Database
Feature Name : UpdateServices-WidDatabase
Feature Name : Microsoft-Windows-Deployment-Services
Feature Name : Microsoft-Windows-Deployment-Services-Deployment-Server
Feature Name : Microsoft-Windows-Deployment-Services-Transport-Server
Feature Name : Microsoft-Windows-Deployment-Services-Legacy-SIS
Feature Name : BitLocker
Feature Name : Bitlocker-Utilities
Feature Name : BitLocker-NetworkUnlock
Feature Name : User-Interfaces-Infra
Feature Name : Server-Gui-Mgmt
Feature Name : RSAT
Feature Name : CoreFileServer-RSAT
Feature Name : Server-Manager-RSAT-File-Services
Feature Name : Server-RSAT-SNMP
Feature Name : DNS-Server-Tools
Feature Name : IPAMClientFeature
Feature Name : WINS-Server-Tools
Feature Name : DfsMgmt
Feature Name : ADCertificateServicesManagementTools
Feature Name : CertificateServicesManagementTools
Feature Name : OnlineRevocationServicesManagementTools
Feature Name : RSAT-AD-Tools-Feature
Feature Name : RSAT-ADDS-Tools-Feature
Feature Name : DirectoryServices-DomainController-Tools
Feature Name : DirectoryServices-ADAM-Tools
Feature Name : BitLocker-RemoteAdminTool
Feature Name : BdeAducExtTool
Feature Name : ActiveDirectory-PowerShell
Feature Name : DirectoryServices-DomainController
Feature Name : DirectoryServices-ISM-Smtp
Feature Name : DirectoryServices-AdministrativeCenter
Feature Name : RasServerAdminTools
Feature Name : DamgmtTools
Feature Name : HCSUI
Feature Name : Licensing-UI
Feature Name : Licensing-Diagnosis-UI
Feature Name : Microsoft-Windows-Deployment-Services-Admin-Pack
Feature Name : DHCPServer-Tools
Feature Name : FailoverCluster-Mgmt
Feature Name : NetworkLoadBalancingManagementClient
Feature Name : NFS-Administration
Feature Name : UpdateServices-UI
Feature Name : WindowsServerBackupSnapin
Feature Name : FaxServiceConfigRole
Feature Name : NPSManagementTools
Feature Name : RightsManagementServicesManagementTools
Feature Name : Security-SPP-Vmw
Feature Name : FSRM-Infrastructure
Feature Name : FSRM-Management
Feature Name : Microsoft-Windows-FCI-Client-Package
Feature Name : Printing-Client
Feature Name : Printing-Client-Gui
Feature Name : RSAT-NIS
Feature Name : MicrosoftWindowsPowerShellISE
Feature Name : Microsoft-Hyper-V
Feature Name : Microsoft-Hyper-V-Offline
Feature Name : Microsoft-Hyper-V-Online
Feature Name : RSAT-Hyper-V-Tools-Feature
Feature Name : Microsoft-Hyper-V-Management-Clients
Feature Name : Microsoft-Hyper-V-Management-PowerShell
Feature Name : VmHostAgent
Feature Name : Server-Gui-Shell
Feature Name : Internet-Explorer-Optional-amd64
Feature Name : FaxServiceRole
Feature Name : ServicesForNFS-ServerAndClient
Feature Name : ServerForNFS-Infrastructure
Feature Name : ClientForNFS-Infrastructure
Feature Name : SearchEngine-Server-Package
Feature Name : FSRM-Infrastructure-Services
Feature Name : NPAS-Role
Feature Name : IAS NT Service
Feature Name : iSCSITargetServer-PowerShell
Feature Name : OEM-Appliance-OOBE
Feature Name : PSync
Feature Name : AppServer
Feature Name : Microsoft-Windows-ServerEssentials-ServerSetup
Feature Name : PKIClient-PSH-Cmdlets
Feature Name : KeyDistributionService-PSH-Cmdlets
Feature Name : TlsSessionTicketKey-PSH-Cmdlets
Feature Name : RemoteAccessMgmtTools
Feature Name : RemoteAccessPowerShell
Feature Name : MicrosoftWindowsPowerShellV2
Feature Name : Server-Psh-Cmdlets
Feature Name : UpdateServices-RSAT
Feature Name : UpdateServices-API
Feature Name : DirectoryServices-ADAM
Feature Name : AuthManager
Feature Name : ServerCore-WOW64
Feature Name : ServerCore-EA-IME-WOW64
Feature Name : LegacyComponents
Feature Name : DirectPlay
Feature Name : Windows-Identity-Foundation
Feature Name : SimpleTCP
Feature Name : Printing-LPRPortMonitor
Feature Name : Printing-InternetPrinting-Client
Feature Name : Printing-AdminTools-Collection
Feature Name : ServerManager-Core-RSAT
Feature Name : ServerManager-Core-RSAT-Role-Tools
Feature Name : ServerManager-Core-RSAT-Feature-Tools
Feature Name : NetFx3ServerFeatures
Feature Name : NetFx3
Feature Name : EnhancedStorage
Feature Name : Microsoft-Windows-GroupPolicy-ServerAdminTools-Update
Feature Name : RasCMAK
Feature Name : RSAT-RDS-Tools-Feature
Feature Name : FailoverCluster-AdminPak
Feature Name : FailoverCluster-PowerShell
Feature Name : AdminUI
Feature Name : BiometricFramework
Feature Name : WindowsServerBackup
Feature Name : WindowsFeedbackForwarder
Feature Name : FileAndStorage-Services
Feature Name : Storage-Services
Feature Name : File-Services
Feature Name : CoreFileServer
Feature Name : File-Services-Search-Service
Feature Name : DFSN-Server
Feature Name : DFSR-Infrastructure-ServerEdition
Feature Name : FileServerVSSAgent
Feature Name : iSCSITargetServer
Feature Name : SMBHashGeneration
Feature Name : Dedup-Core
Feature Name : DHCPServer
Feature Name : DNS-Server-Full-Role
Feature Name : FailoverCluster-AutomationServer
Feature Name : FailoverCluster-CmdInterface
Feature Name : FRS-Infrastructure
Feature Name : Windows-Internal-Database
Feature Name : WINSRuntime
Feature Name : iSCSITargetStorageProviders
Feature Name : iSNS_Service
Feature Name : BITS
Feature Name : LightweightServer
Feature Name : MultipathIo
Feature Name : NetworkLoadBalancingFullServer
Feature Name : NIS
Feature Name : PeerDist
Feature Name : P2P-PnrpOnly
Feature Name : Printing-XPSServices-Features
Feature Name : QWAVE
Feature Name : MSRDC-Infrastructure
Feature Name : RemoteAssistance
Feature Name : ServerCore-EA-IME
Feature Name : DataCenterBridging
Feature Name : ServerMediaFoundation
Feature Name : InkAndHandwritingServices
Feature Name : DesktopExperience
Feature Name : MediaPlayback
Feature Name : WindowsMediaPlayer
Feature Name : ServerMigration
Feature Name : ServerCore-Drivers-General
Feature Name : Server-Drivers-General
Feature Name : Server-Drivers-Printers
Feature Name : SIS-Limited
Feature Name : SmbDirect
Feature Name : SNMP
Feature Name : WMISnmpProvider
Feature Name : WindowsStorageManagementService
Feature Name : TelnetClient
Feature Name : TelnetServer
Feature Name : Remote-Desktop-Services
Feature Name : SessionDirectory
Feature Name : SBMgr-UI
Feature Name : Licensing
Feature Name : TFTP
Feature Name : VolumeActivation-Full-Role
Feature Name : TIFFIFilter
Feature Name : WirelessNetworking
Feature Name : Xps-Foundation-Xps-Viewer
Feature Name : SMB1Protocol
Feature Name : SMBBW
Feature Name : FailoverCluster-FullServer
Feature Name : CCFFilter
Feature Name : ResumeKeyFilter
Feature Name : SmbWitness