Over the various versions of windows server there have been many different event IDs logged when accounts are locked out after too many failed logon attempts. The event you are after for 2008 R2 / 2012 is Event ID 4740 and it is logged in the security event log.
It is possible to use a simple scheduled task which runs with this event ID as the trigger to generate an “account is locked” email, but why do that when you have operations manager?
We can create a new rule to alert on this event and it is also even possible to base the alert on other items within the event description. For example you might want a generic account is locked email to go to the support desk, whereas alerts for a critically important service account should go to a separate team who manage this service. Here is a guide on how to setup such an alert.
1. Load up the operations manger console and click on “Authoring”
2. Expand the “Management Pack Objects” item and click on “Rules.”
3. Click on “Create a rule.” This is in the tasks pane on the right hand side, you might need to expand this if you have previously closed it.
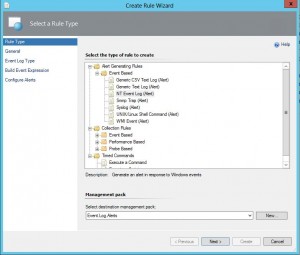
4. Expand “alert Generating Rules” then expand “Event based” and select “NT Event log (alert)” and select an appropriate management pack to store the alert. I would reccomend creating a management pack for all your custom rule based alerts or if you plan on having many it maybe worth breaking it out further, e.g. “Account Lockout Alerts”
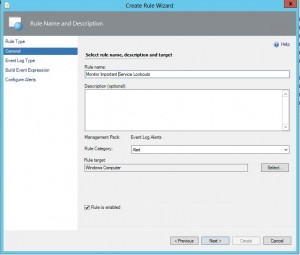
5. Click “Next” and give your new rule a suitable name.
6. Select a rule target, in this instance “Windows Computer” will work and click “Next.”
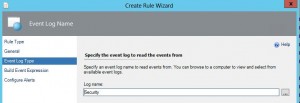
7. Select the Log you wish to monitor, for this rule we need to select the security log then click “Next.”
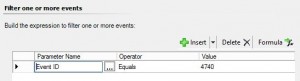
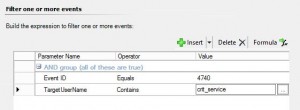
8. Now it is time to build the expression to filter the events we want to alert on. If you simply want an alert any time this occurs set the parameter name to “Event ID” Operator to “Equals” and Value to “4740”.
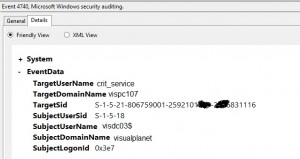
9. If however you want to be a little more presisce and only generate an alert for a particualr account or computer (or anything within the event) you can. Simply locate an event you want to build an expression for on one of your target servers (e.g. log onto a DC and have a look for a security event with ID4740) and examine the details section.
10. Here I want to configure the alert to only fire if the “crit_service” account is locked. So within the expression builder I insert a new expression and select an event property and enter my own.
Parameter Name: “TargetUserName”
Operator: “Contains”
Value “crit_service”
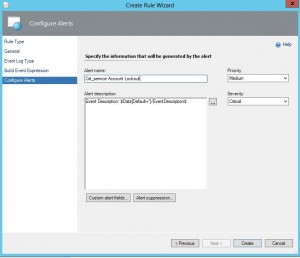
11. Finally configure the alert. Here you can edit the alert name, description and other fields. I simply changed the alert name and left the alert description and other fields alone as it is fine for my purposes.
12. Dont forget to setup an alert subscription for this so the right people get an alert when the account is locked out! If you took a note of the alert name used you can filter against this to make sure only the right people get the message.

Thanks a lot.
TargetUserName not working.. without user filter all works great
Igor…instead of selecting “Use parameter name not specified above” Select “Specify event specific parameter to use:” and use parameter number 1.
Nice post. Thanks
Helped me to set up this in our Live environment. Thank you. It really helped to send notifications to helpdesk so that they know where the lock out was coming from when user called them.
I have 500+ service accounts in my environment. I am using SCOM 2012. From you solution i see we can do it for one account. In my case where we have bulk, how can we set it up ?
Hi,
I need to set up for particular task ( SChduled task) but its not working for any parameter apert form event id and event source
any help would be appriciated
Parameter 1is working
Thanks
Has anyone run into an issue where you receive the same alert from a PDC as well as another Domain controller? If so, how do you only receive one alert? I’ve tried various suppression methods but cannot seem to figure it out.
Thanks
B.Web is right – Use parameter 1